Back when computer interfaces were nothing but keyboards, a string of characters seemed like the optimal solution to authenticate users.
For decades our digital rituals evolved with the interfaces, while passwords still remain unchallenged.
What if we could design new ways to replace the password, using modern hardware and software like machine learning?
Projects
Projects
Divided we fall

What if passwords become collaborative?
Passwords are commonly seen as a private and individual entity, designed in order to keep our privacy secret. What if passwords are shared across communities or groups of people? What if a group of people is required to authenticate?
In order to unlock the screen, multiple participants have to combine their bodies in a secret combination of postures.
When the user is not authenticated, the application displays an incomplete message, that becomes readable only when more participants join the scene.
"Divided we fall" is built using ml5js with Posenet. The source code is available here.
The more users join the scene, the more the message becomes readable.
Knock Knock
what if your password has rhythm?
"Knock Knock" reinterprets the old way of asking to come in by knocking on a door by adapting to users' individual rhythms of knocking and usage.
Knock Knock was developed on Arduino, with Wekinator trained to identify sound patterns through MFCCs (Mel-frequency Cepstral Coefficients) and Processing.
Full Body Unlock


What if the password is your body?
Be proud of your password! Don't keep it to yourself, express it using your whole body.
Our full body password input interface allows you to express your password using your whole body, rather than just keeping it a secret between your computer and your fingertips.
Performing your password with your whole body in front of a room full of people will help you overcome the tired old taboo of entering a password while people are watching.
Glyphword
What if the digital key becomes a physical key?
Imagine being able to make your own physical key for your personal computer or digital device, and to map a secret gesture that enhances the security level.
Glyphord is made by a combination of physical paper key and a secret gesture, to be performed with the key in front of the camera, to unlock all your secrets.
The project uses the ml5.js library, with the Feature Regression Extraction model.
Drake Gate
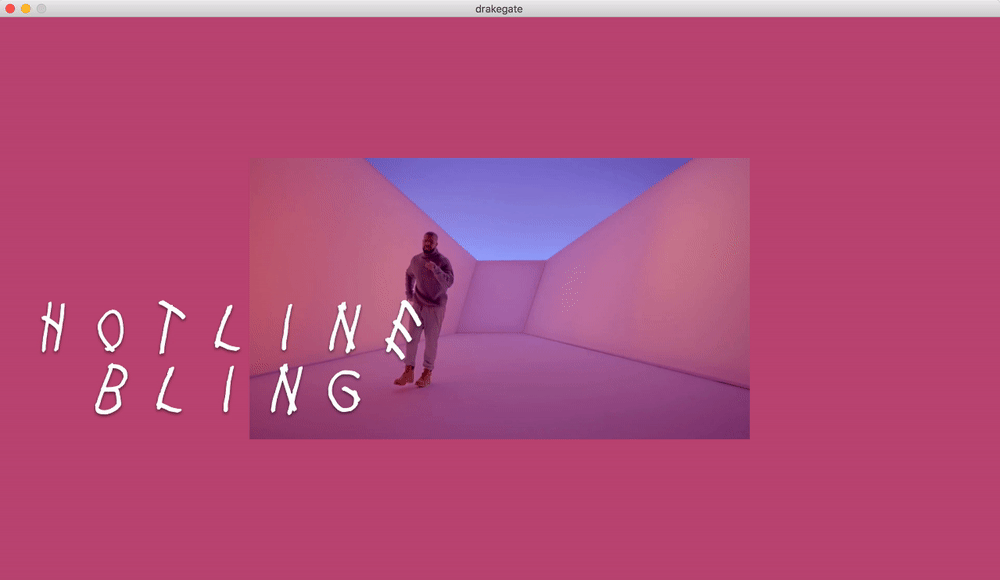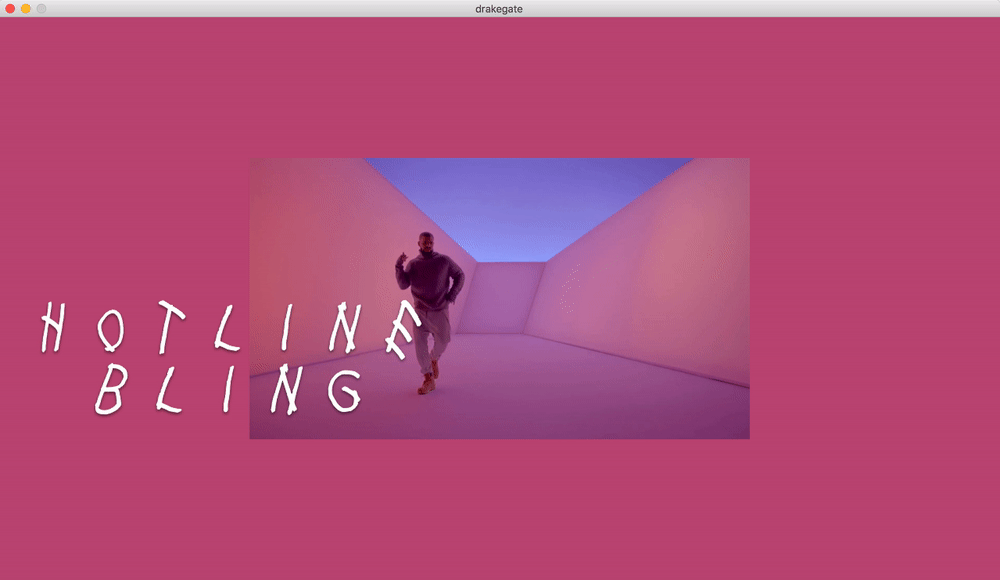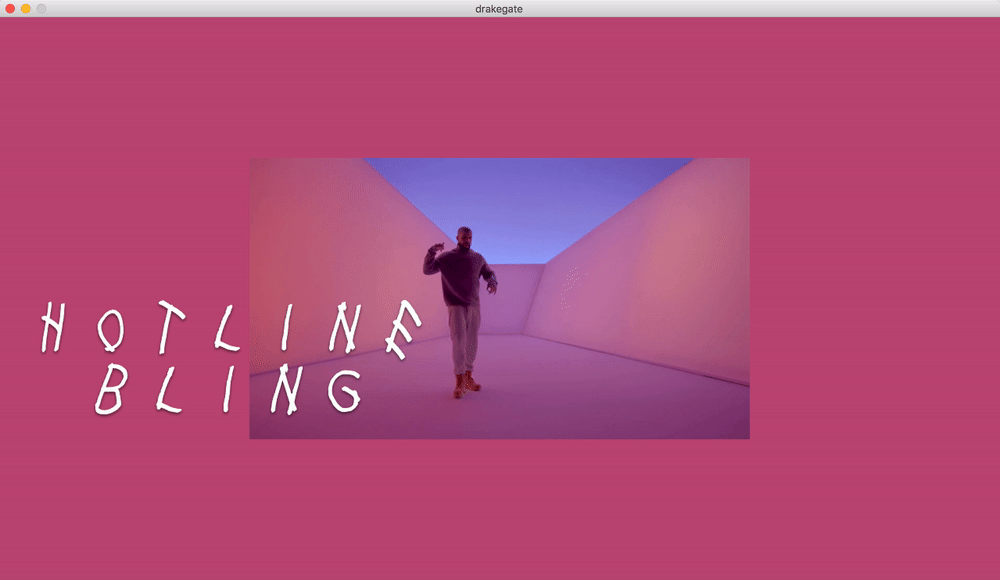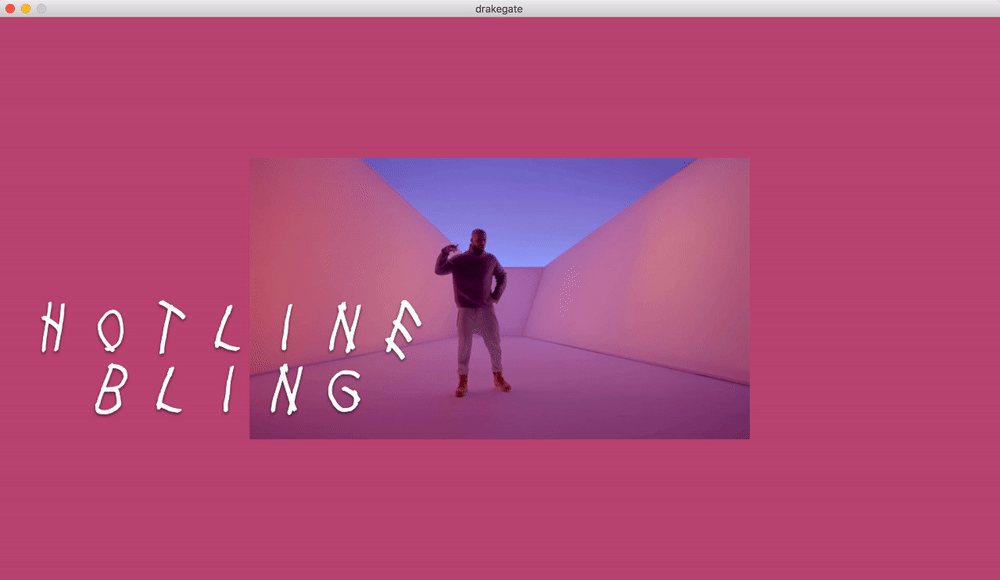

What if drake moves are now your password?
Only the computer and the user know the real official 100% certified Drake moves.
The main idea was to experiment with movements and motion tracking. We created an unlock game where the machine asks the user to make a typical Drake move in order to unlock the computer.
We modified and merged a couple of P5js sketches in order to send the data to Wekinator via OSC, we did also two outputs sketches, one in p5js and the other one in Processing.
Bribes
do machines hallucinate?
Bribes prompts you to imagine what the system wants from you.
An object isn’t secure enough to use as a password for unlocking your own things, but the objects you choose when prompted by a system can reveal something about your thinking. The owner of the system can decide to let you in or lock you out.
Bribes uses ConvnetOSC with Wekinator, trained to identify the passcode objects for the gatekeepers.
The Animal Kingdom Hacker Collective (AKHC) recruits by infecting computers with viruses, allowing your computer to “hallucinate” AKHC gatekeepers when you browse the web.
If you give the gatekeepers what they want, they’ll invite you in.
FitDay
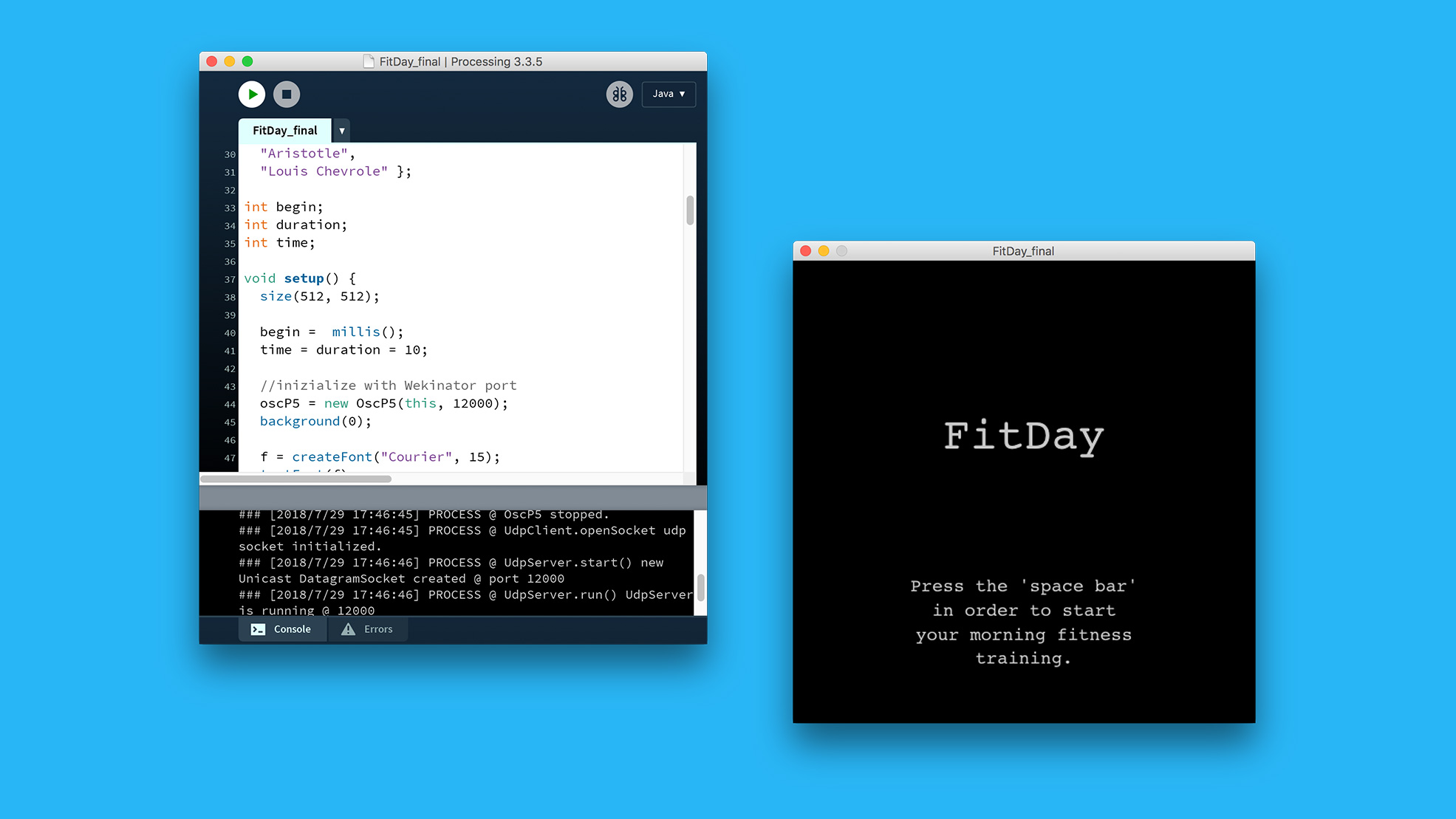
are you healthy enough to unlock your machine?
In a dystopian world in a near future, every home is equipped with objects and furniture connected to the internet of things.
You have to perform daily movements in order to receive a reward and unlock something useful for living, such as points for having your kitchen robot generating a tasty dish.
Every device understands, read and learn the use you make of them, in order to provide better-personalised services. But what if their real goal is something different?
FitDay is a Processing application using Wekinator to identify three types of gestures. The movements are captured by MotionSender, an application sending accelerometer data to Wekinator.
Once the right gestures are performed for a certain amount of time, a random quote about movement is then displayed to the user.
The Shakingway Test

can machines simulate dead writers?
Ernest Hemingway and William Shakespeare have collaborated on writing a novel, each of them writing one or more lines, then passing the manuscript on to the other.
Your task is to figure out which lines have been written by whom. Only those getting it right will be deemed worthy of entering!
Flower Power

Can living organisms become your password?
Unlock and get access to anything with just a flower.
With Flower Power you can just show a specific flower (or the picture of it), to unlock the screen.
The project was deeply trained using pictures from the Instagram account @flamboyantflowersapp to recognize three different types of flowers.
This input was captured, classified and trained by the machine learning tool Wekinator using 5 classes.
The resulting trained models are then being parsed in Processing, in order to generate the output.
Rock Paper Scissors
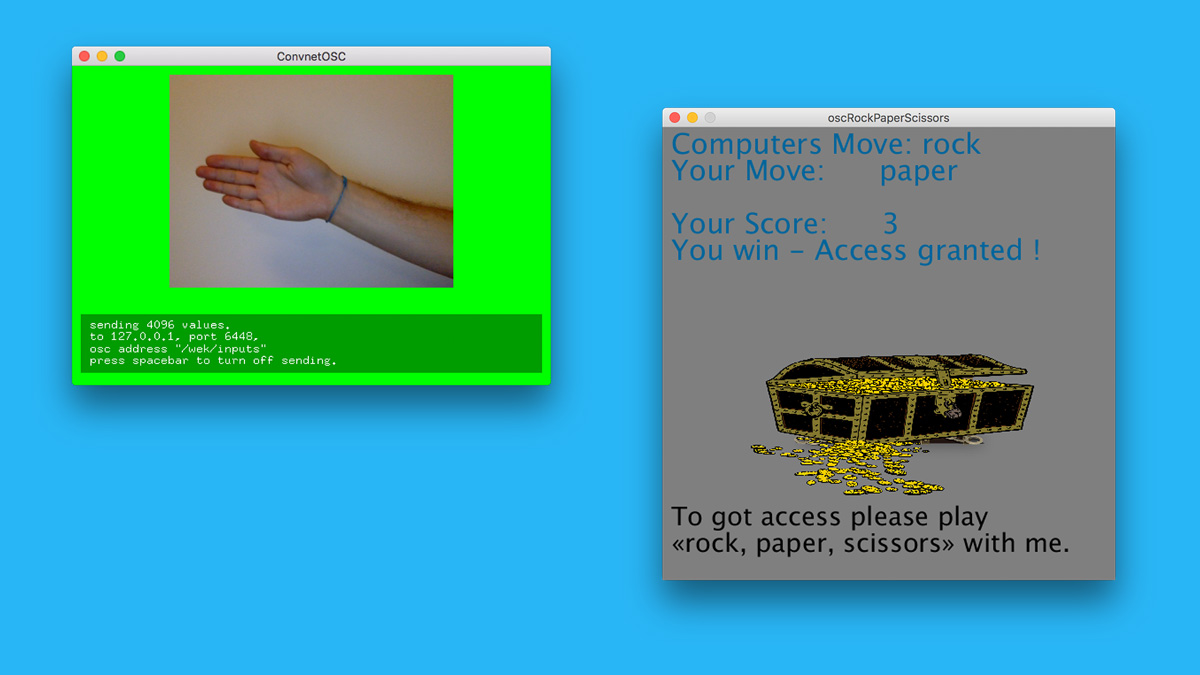
can machines be really defeated?
Soon, our concept of privacy will vanish.
In a world without privacy, passwords to get access becomes senseless, but rituals – like logging in – are still important.
So instead of user accounts and passwords to get access, you soon will have to defeat your computer in little games like «Rock, paper, scissors», to get access.
One Two Three
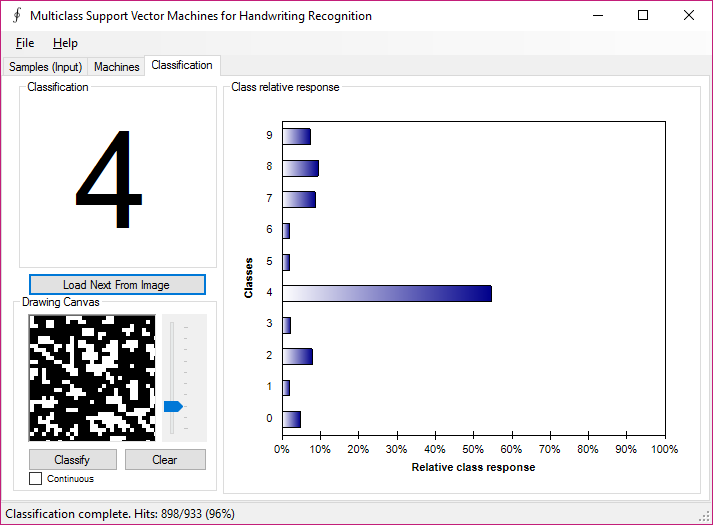
how much can we trust scientific models?
Based on a sample solution to encode handwritten letters from 0-9 an extension has been added to stress the learned model with pseudo-random images (cut out from a forest image in black and white).
The solutions show that learned models are always a very limited representation of the world and the selection of the data for the learning requires the highest caution.
thanks!